|
 With the Studio Display and ?Studio Display? XDR set to launch on Wednesday, members of the media have started publishing their reviews of the new display options. With the Studio Display and ?Studio Display? XDR set to launch on Wednesday, members of the media have started publishing their reviews of the new display options.
|
|
 The first reviews of the new 14-inch and 16-inch MacBook Pro models with Apple's M5 Pro and M5 Max chips were published today by selected publications and YouTube channels, ahead of the laptops launching on Wednesday. The first reviews of the new 14-inch and 16-inch MacBook Pro models with Apple's M5 Pro and M5 Max chips were published today by selected publications and YouTube channels, ahead of the laptops launching on Wednesday.
|
|
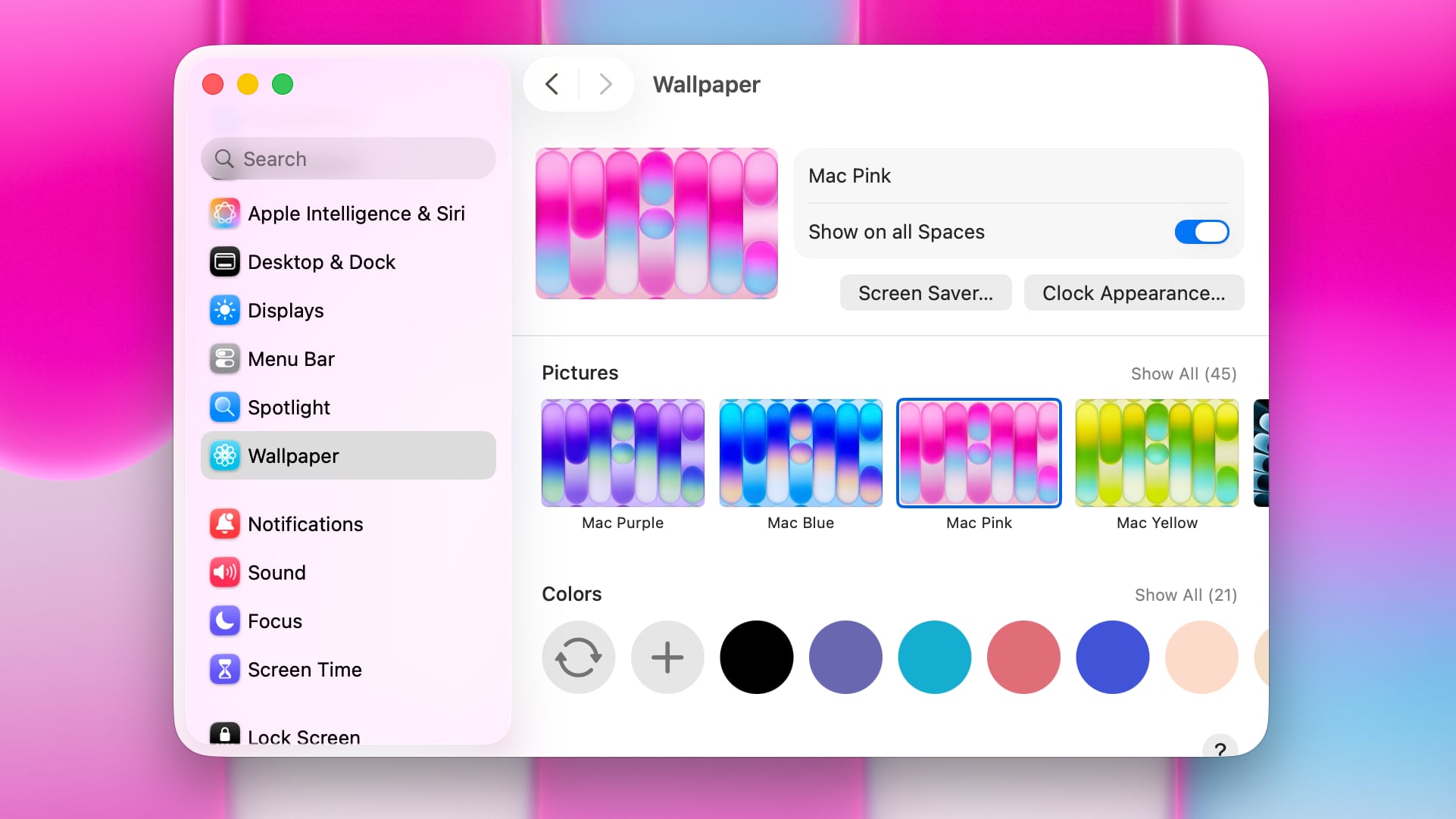 The colorful new wallpapers that Apple introduced with the MacBook Neo are available for all Macs in the fourth beta of macOS Tahoe 26.4 that came out for developers today. The colorful new wallpapers that Apple introduced with the MacBook Neo are available for all Macs in the fourth beta of macOS Tahoe 26.4 that came out for developers today.
|
RELATED ARTICLES | | |
|
 Apple is postponing the launch of its planned smart home hub until September 2026, reports Bloomberg. Apple has pushed back the debut of the home hub multiple times due to ongoing issues with the revamped version of Siri. The hub has a heavy AI focus and it is tied to the more intelligent ?Siri? that Apple has in the works. Apple is postponing the launch of its planned smart home hub until September 2026, reports Bloomberg. Apple has pushed back the debut of the home hub multiple times due to ongoing issues with the revamped version of Siri. The hub has a heavy AI focus and it is tied to the more intelligent ?Siri? that Apple has in the works.
|
|
 If you want a MacBook Neo for delivery on Wednesday, March 11 launch day, but have yet to place an order, you might be out of luck. If you want a MacBook Neo for delivery on Wednesday, March 11 launch day, but have yet to place an order, you might be out of luck.
|
RELATED ARTICLES | | |
|
 Apple today provided developers with the fourth betas of upcoming watchOS 26.4 and visionOS 26.4 betas for testing purposes. The software comes a week after Apple released the third betas. Apple today provided developers with the fourth betas of upcoming watchOS 26.4 and visionOS 26.4 betas for testing purposes. The software comes a week after Apple released the third betas.
|
RELATED ARTICLES | | |
|
 Apple today seeded the fourth betas of upcoming iOS 26.4 and iPadOS 26.4 updates to developers for testing purposes, with the software coming a week after Apple provided the third betas to developers. Apple today seeded the fourth betas of upcoming iOS 26.4 and iPadOS 26.4 updates to developers for testing purposes, with the software coming a week after Apple provided the third betas to developers.
|
|
 Tech columnist David Pogue's new book Apple: The First 50 Years will be available in hardcover and digital formats starting this Tuesday, March 10. Tech columnist David Pogue's new book Apple: The First 50 Years will be available in hardcover and digital formats starting this Tuesday, March 10.
|
|
