|
How Apple's lower-cost iPhone 17E matches up with its more-expensive sibling phones.
|
|
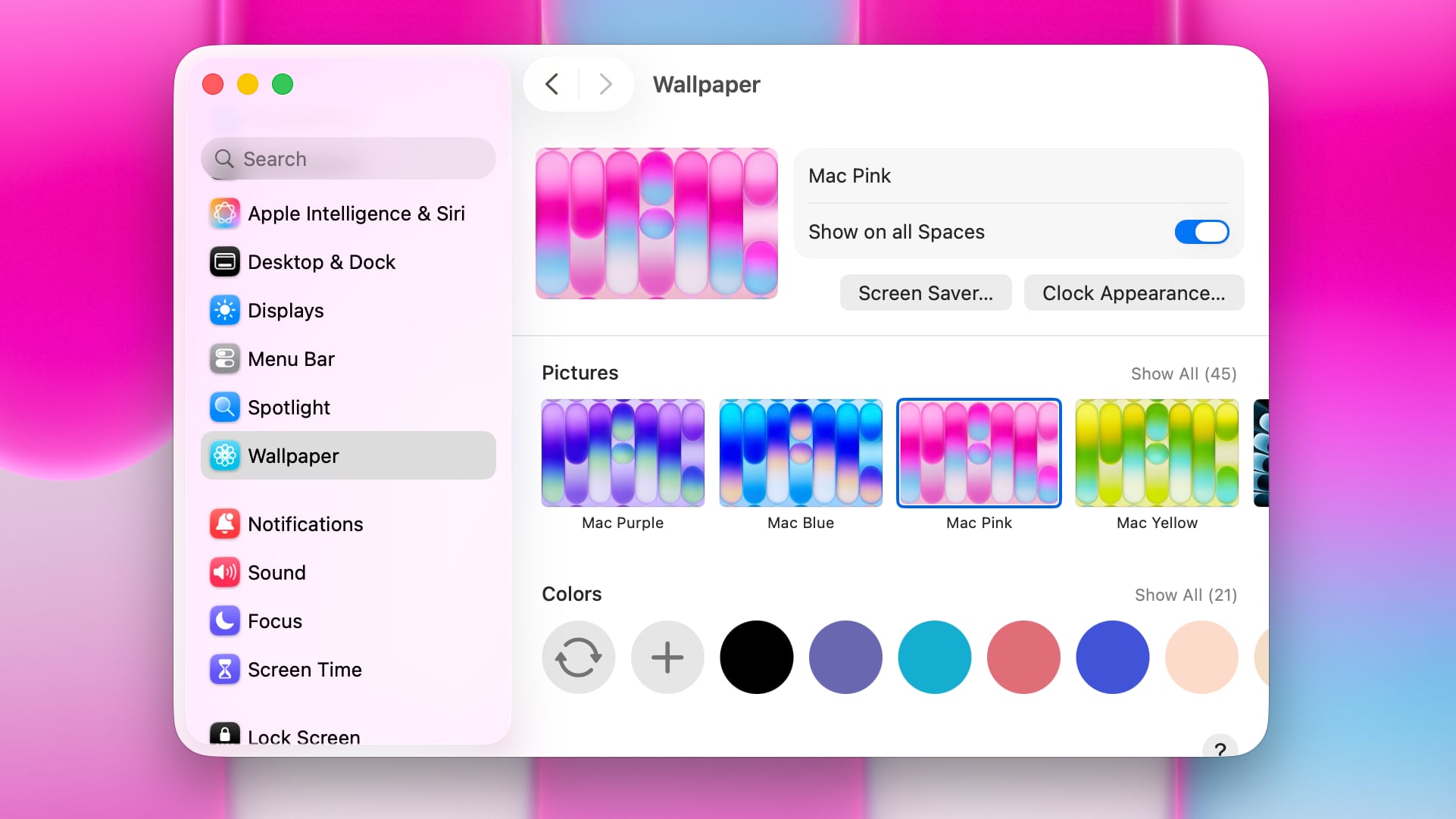 The colorful new wallpapers that Apple introduced with the MacBook Neo are available for all Macs in the fourth beta of macOS Tahoe 26.4 that came out for developers today. The colorful new wallpapers that Apple introduced with the MacBook Neo are available for all Macs in the fourth beta of macOS Tahoe 26.4 that came out for developers today.
|
RELATED ARTICLES | | |
|
 The first reviews of the new 14-inch and 16-inch MacBook Pro models with Apple's M5 Pro and M5 Max chips were published today by selected publications and YouTube channels, ahead of the laptops launching on Wednesday. The first reviews of the new 14-inch and 16-inch MacBook Pro models with Apple's M5 Pro and M5 Max chips were published today by selected publications and YouTube channels, ahead of the laptops launching on Wednesday.
|
|
 What a week for Apple news! Across Monday, Tuesday, and Wednesday of this week, Apple unveiled a total of seven new products, including low-cost iPhone and MacBook options, new displays, and refreshes for the MacBook Air, MacBook Pro, and iPad Air. What a week for Apple news! Across Monday, Tuesday, and Wednesday of this week, Apple unveiled a total of seven new products, including low-cost iPhone and MacBook options, new displays, and refreshes for the MacBook Air, MacBook Pro, and iPad Air.
|
|
