|
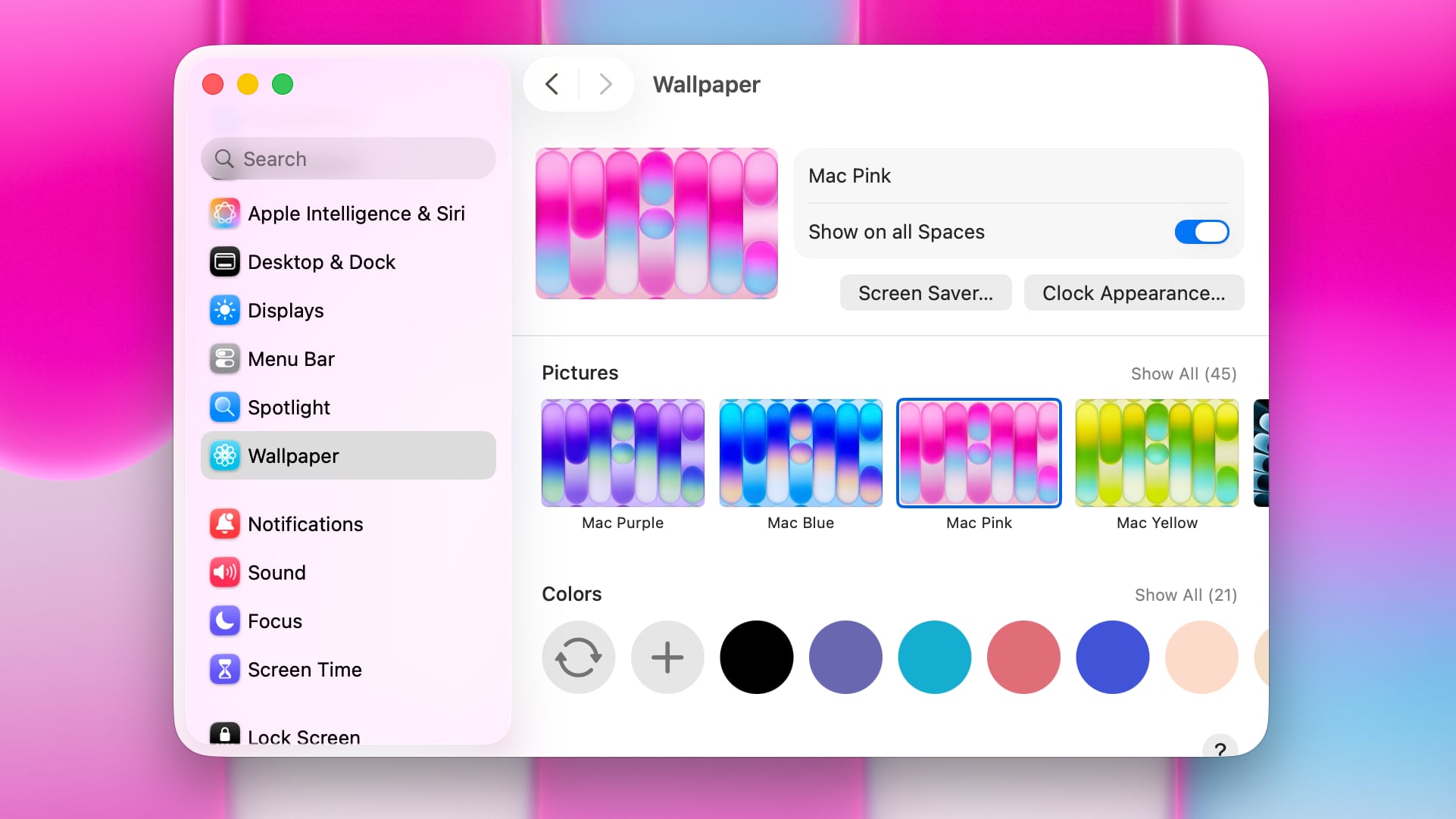 The colorful new wallpapers that Apple introduced with the MacBook Neo are available for all Macs in the fourth beta of macOS Tahoe 26.4 that came out for developers today. The colorful new wallpapers that Apple introduced with the MacBook Neo are available for all Macs in the fourth beta of macOS Tahoe 26.4 that came out for developers today.
|
|
Enemies can be friends when their interests align.
|
RELATED ARTICLES | | |
|
OpenAI hardware leader Caitlin Kalinowski has resigned after the company's Pentagon AI deal, citing concerns over surveillance, autonomy, and governance.
The post OpenAI Robotics Leader Resigns, Says Ethical ‘Lines' Were Crossed in Pentagon Deal appeared first on eWEEK.
|
|
 Apple today provided the fourth beta of an upcoming macOS Tahoe 26.4 update to developers for testing purposes, with the update coming a week after Apple seeded the third beta. Apple today provided the fourth beta of an upcoming macOS Tahoe 26.4 update to developers for testing purposes, with the update coming a week after Apple seeded the third beta.
|
|
Bluesky CEO Jay Graber, who has led the upstart social platform since 2021, is stepping down from her role as its top executive. Toni Schneider, who has been an advisor and investor in Bluesky, will take over the job temporarily while Graber stays on as Chief Innovation Officer.
"As Bluesky matures, the company needs a seasoned operator focused on scaling and execution, while I return to what I do best: building new things," Graber wrote in a blog post. Schneider, who was previously CEO at Wordpress parent Automattic, will be that "experienced operator and leader" while Blueksy's board searches for a permanent CEO, she said.
Graber's history with Bluesky dates back to its early days as a side project at Jack Dorsey's Twitter. She was officially brought on as CEO in 2021 as Bluesky spun off into an independent company (it officially ended its association with Twitter in 2022 and Dorsey cut ties with Bluesky in 2024). She led the company through its launch and early viral success as it grew from an invitation-only platform to the 43 million-user service it is today. During that time, she's become known as an advocate for decentralized social media and for trolling Mark Zuckerber
|
|
